Redefine Data Security Posture Management (DSPM) by not only detecting but neutralizing data threats in real-time, for unparalleled protection beyond ransomware. Our scalable platform combines DSPM and Data Detection and Response (DDR), providing continuous monitoring and robust ransomware protection across all data architectures. We guarantee business continuity, foster stakeholder trust, and support your organization's growth in the digital landscape.
Why We're Different
AI Data Discovery & Classification - Efficient, accurate, industry-specific language learning models (LLM)
Ransomware Protection - 77 seconds to detect, isolate, and stop attacks
Data Security for All Data Types - Protect structured and unstructured data, in the cloud and on-premises with patented queryable encryption
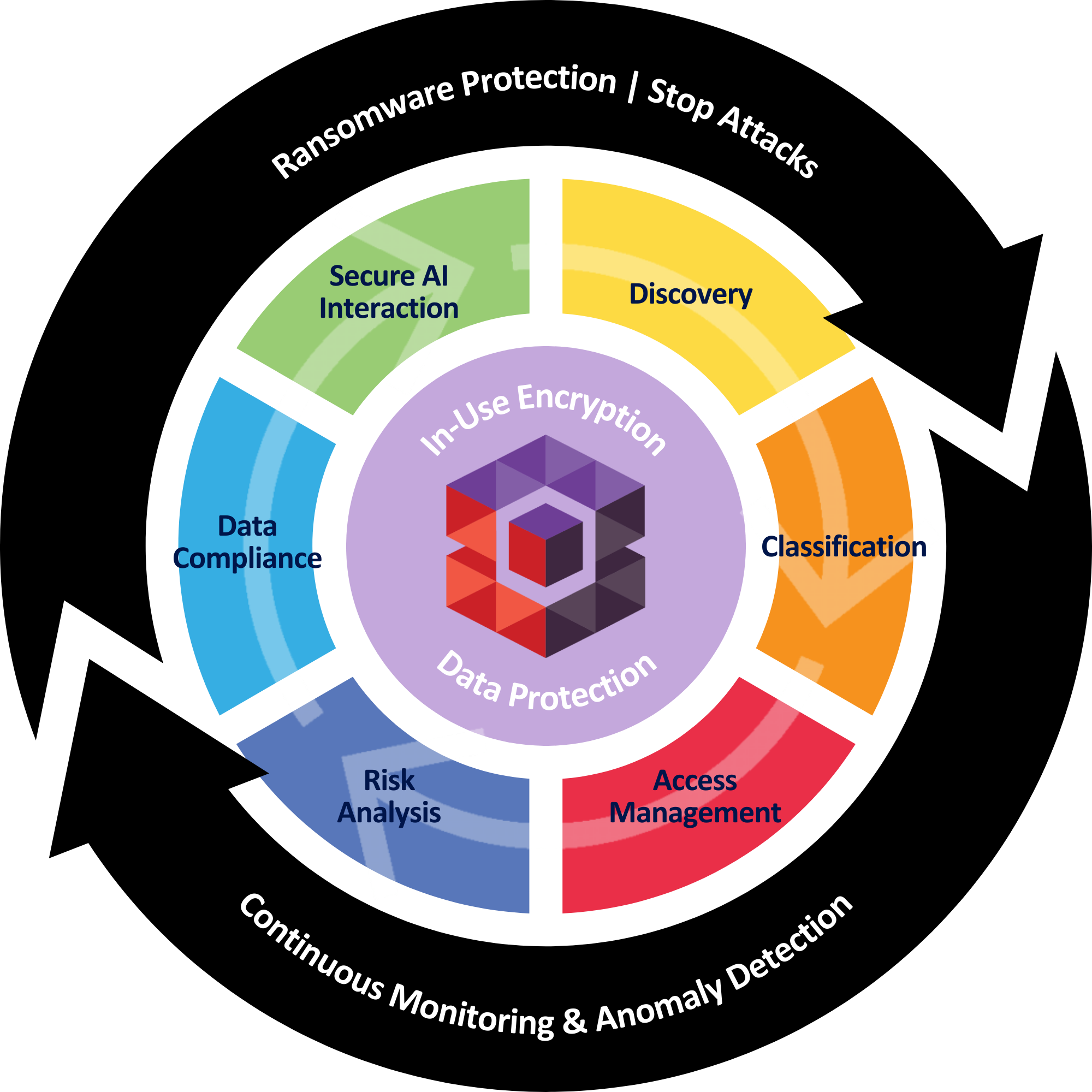
Business Impact of Sotero’s All In One Data Security Platform
Comprehensive Data Protection
Sotero's DSPM and DDR capabilities offer an all-in-one platform for data security. This not only enables real-time threat detection but also actively neutralizes these threats, providing robust, multi-layered protection against malicious activities beyond ransomware.
Continuous Monitoring & Adaptive Security
Sotero's solution continuously monitors your data security posture and dynamically adapts to emerging threats. This ensures that your data security measures remain up-to-date and effective, enhancing overall cyber resilience.
Uninterrupted Business Continuity
By detecting and stopping cyber threats in their tracks, Sotero helps prevent disruptions to business operations. This guarantees seamless business continuity, even in the face of rapidly evolving digital threats.
Stakeholder Trust
By providing comprehensive and effective data protection, Sotero helps bolster trust among your customers, partners, and employees. This trust is crucial to maintain and enhance your organization's reputation in today's digital environment.
A DSP That Scales with Your Organization
By ensuring robust data security, Sotero allows businesses to confidently expand their digital operations without fear of data breaches. This effectively removes a major barrier to digital transformation, letting your organization fully leverage new opportunities.
Meet Regulatory Compliance
With robust data protection, Sotero aids organizations in meeting regulatory requirements for data security. This not only helps avoid penalties but also ensures a positive standing with regulatory bodies.
Cost Efficiency
By offering DSPM and DDR from a single platform, Sotero helps organizations save on the cost of investing in multiple solutions, while also reducing the time and resources needed to manage separate platforms.
Sotero's comprehensive data protection solution offers significant benefits to organizations looking to safeguard their sensitive data and maintain a strong and adaptable security posture.
Sotero’s DSPM+ Capabilities
AI Data Discovery & Classification
AI enabled to let technical and non-technical users define and manage sensitivity levels of specific data attributes.
Proactively scan and flag sensitive information, for effective risk mitigation and data protection.
Risk Analysis
Prioritize each data access request, identify potential vulnerabilities and categorize them based on their severity and threat potential.
This allows your organization to focus on addressing the most critical risks first.
Data Security For All Data Types
Comprehensive data security for both structured and unstructured data, whether on premises, in the cloud, or in hybrid environments.
Continuous Monitoring and Governance
Monitor user's and application’s access requests and changes to your data with real-time threat detection combined with advanced machine learning (ML).
Compliance
An extensive audit dashboard lets you stay in control of your data with granular insights. Avoid fines, get a competitive advantage, and get or stay compliant.
Connect Everything for Full Visibility and Control
Sotero monitors the behavior of every database, file store, and application without agents to provide complete visibility into every technology that touches your structured or unstructured data, whether on-premises, in the cloud, or in hybrid environments.
Sotero is deployment agnostic, and works seamlessly with structured and unstructured data. Our DSP connects with data stores like public or private cloud storage systems, network file storage systems, and databases. Our platform is built with an API-first architecture approach, letting you leverage APIs to automate your system integration to provide seamless data protection across your environment. Sotero supports organizations as they scale from SMB to multi-national enterprises to provide complete data security to make your data our priority. Sotero’s DSP also seamlessly integrates with:
- Existing directory services/IdP for RBAC controls
- Existing SIEM/UEBA solutions
- Existing key management solutions for FIPS 140-2 or 140-3 level 2 or level 3 requirements









.png?width=1200&length=1200&name=gcp%20(1).png)





.svg.webp?width=1200&length=1200&name=Microsoft_logo_(2012).svg.webp)


.png?width=1200&length=1200&name=Apache_kafka_wordtype.svg%20(1).png)







Let us make your data’s security our priority.
Ready To See For Yourself?
Strategy Session
This is your chance to discover how Sotero can help your organization with its data security needs.
We typically cover the following together:
- Review your data security challenges
- Explore potential use cases
- Learn about Sotero
- Discuss next steps



.jpg)








