GUIDE
Data Detection and Response (DDR)
Data Detection and Response (DDR) is a cutting-edge strategy used to protect your sensitive information from the increasing risks posed by cyber threats. With new threat vectors emerging daily, your data is one of your most valuable assets, but it's also a prime target for cybercriminals. DDR helps to safeguard that data by identifying, investigating, and responding to potential security incidents.
Think of DDR as your personal digital security guard who never sleeps. It's constantly monitoring your data and looking for anything unusual. DDR combines elements of data monitoring, threat intelligence, incident detection, and incident response to provide a comprehensive security solution.
2. Investigation: If a potential threat is detected, DDR doesn't just raise the alarm and leave it at that. Instead, it investigates the nature of the threat, determines the severity and credibility of the risk, and identifies the best course of action.
3. Response: Once the threat has been thoroughly investigated, DDR takes action to mitigate the risk. This could include isolating the affected systems, blocking the malicious activity in its tracks, or even launching a countermeasure to neutralize the threat.
In short, Data Detection and Response is your all-in-one solution to keep your data safe by stopping attacks in a constantly evolving threat landscape. It's like having a top-notch security team on your side, dedicated to protecting your most valuable digital assets around the clock.
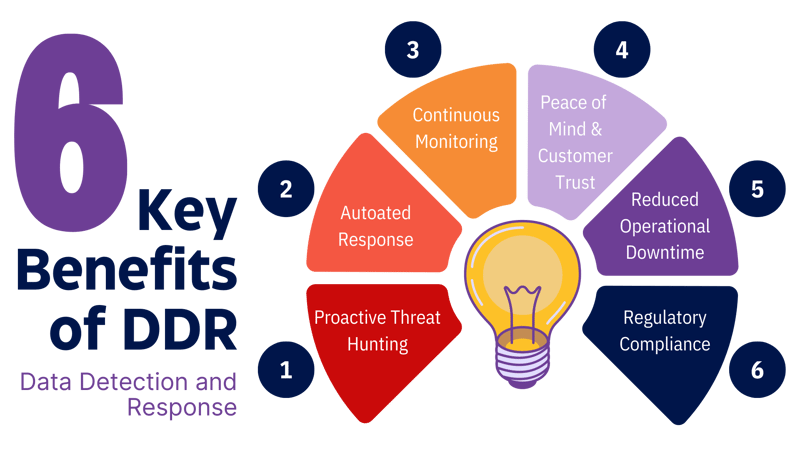
Technical and Business Benefits of DDR
Data Detection and Response (DDR) is an essential layer of security for your business in addition to Data Security Posture Management (DSPM). It brings several key benefits that can help both technically and at the business level:
Technical Benefits
1. Proactive Threat Hunting
DDR isn't just about reacting to threats, it's about actively looking for them. This proactive approach can help identify potential issues before they become serious problems, keeping your data safe and your systems running smoothly. DDR solutions leverage advanced analytics techniques, such as machine learning and behavior analysis, to monitor network traffic, system logs, and data sources in real-time. By establishing a baseline of normal behavior, DDR systems can identify anomalies or suspicious activities that might indicate a security breach or unauthorized access. This real-time detection capability allows organizations to swiftly respond to potential threats before they can cause significant damage.
2. Automated Response
Thanks to sophisticated algorithms and machine learning techniques, DDR can automatically respond to identified threats, significantly reducing the time it takes to mitigate a potential breach. DDR solutions often employ automation capabilities, such as orchestration and correlation engines, to streamline incident triage and investigation processes. When a potential security incident is detected, these automated tools can collect relevant data, correlate events, and generate detailed incident reports. By automating these initial steps, security teams can reduce manual effort and quickly focus on the critical aspects of incident response, such as containment, eradication, and recovery. Automated incident triage and investigation also help improve consistency and accuracy in threat analysis, leading to more effective incident response outcomes.
3. Continuous Monitoring
DDR provides round-the-clock surveillance of your systems, ensuring that no potential threat goes unnoticed, no matter when or where it occurs. It also provides continuous improvement through machine learning (ML). DDR solutions leverage ML algorithms to continually refine threat detection capabilities. By analyzing vast amounts of security data and historical incident information, these algorithms can adapt and evolve, improving their accuracy over time. ML enables DDR systems to recognize new and emerging threat patterns, ensuring organizations stay ahead of evolving cyber threats. This continuous improvement cycle enhances the effectiveness of data detection and response, bolstering an organization's overall cybersecurity posture.
DDR offers significant technical benefits to organizations seeking robust cybersecurity solutions. By providing real-time threat detection, proactive incident response, enhanced visibility, and automated incident triage, DDR empowers security teams to detect and respond to security incidents swiftly and effectively. The continuous improvement enabled by machine learning (ML) ensures that organizations can stay ahead of emerging cyber threats. By adopting DDR, organizations can fortify their defenses, protect sensitive data, and mitigate the potential impact of cybersecurity incidents.
Business Benefits
4. Peace of Mind & Customer Trust: Knowing that your data is protected by DDR gives you the confidence to focus on what you do best - running your business. You can rest easy knowing that your valuable data is in safe hands. In an era when data breaches are frequently in the news, showing your customers that you take their data security seriously can be a major selling point. DDR helps you build and maintain that trust.
5. Reduced Operational Downtime: By identifying and addressing threats early, DDR can help minimize disruptions to your business operations, ensuring that your services remain available to your customers.
6. Regulatory Compliance: Many industries have strict data protection regulations. DDR can help you meet these requirements, avoiding potential fines and protecting your company's reputation.
In summary, DDR is not just a technical solution; more importantly, a business investment. It protects your assets, ensures your operations run smoothly, and helps build trust with your customers - all of which contribute to your bottom line.
Business Benefits
4. Peace of Mind & Customer Trust
Knowing that your data is protected by DDR gives you the confidence to focus on what you do best - running your business. You can rest easy knowing that your valuable data is in safe hands. In an era when data breaches are frequently in the news, showing your customers that you take their data security seriously can be a major selling point. DDR helps you build and maintain that trust.
5. Reduced Operational Downtime
By identifying and addressing threats early, DDR can help minimize disruptions to your business operations, ensuring that your services remain available to your customers.
6. Regulatory Compliance
Many industries have strict data protection regulations. DDR can help you meet these requirements, avoiding potential fines and protecting your company's reputation.
In summary, DDR is not just a technical solution; more importantly, a business investment. It protects your assets, ensures your operations run smoothly, and helps build trust with your customers - all of which contribute to your bottom line.
How DDR Works
Data Detection and Response (DDR) is a sophisticated system that works tirelessly to protect your sensitive data from potential threats. But how does it actually work?
- Collect and Monitor: The first step in DDR is to continuously monitor and collect data from your systems. This could be data about who is accessing your system when they're accessing it, and what they're doing. It's a bit like a security camera in a store, always watching and recording what's happening.
- Analyze: Once the data is collected, DDR uses advanced algorithms and machine learning techniques to analyze it. This is where DDR really shines. It can look at patterns, behaviors, and anomalies to identify potential threats that might not be obvious to the human eye. It's similar to a detective looking for clues in a complex case.
- Detect: If the analysis reveals something unusual, like an access attempt from an unfamiliar location or a sudden surge in data transfer, DDR flags it as a potential threat. Just like a guard dog barking when a stranger approaches your house, DDR raises the alarm when it detects something suspicious.
- Investigate: Once a potential threat has been detected, DDR doesn't just stop there. It investigates further, trying to understand the nature of the threat and how serious it is. It's like a security team checking out what caused the alarm to go off.
- Respond: After investigating, DDR takes the appropriate action. If the threat is real, it might block the suspicious activity, isolate the affected systems, or alert your IT team. In some cases, it can even take action to neutralize the threat. It's like a security guard stepping in to handle a situation before it gets out of hand.
In summary, DDR works as your round-the-clock digital security guard, using cutting-edge technology to protect your valuable data. It's constantly watching, analyzing, detecting, investigating, and responding to keep your data safe and secure.
How DDR Is Used In Practice
Data Detection and Response (DDR) is used in practice in a variety of ways across different industries, offering a proactive approach to cybersecurity. Let's explore some real-world examples:
- Retail Industry: In the retail sector, DDR can be used to protect sensitive customer information such as credit card numbers, addresses, and purchasing history. For example, DDR might detect an unusual spike in data being transferred out of a customer database, flag it as suspicious, and then take action to block this transfer, preventing a potential data breach.
- Healthcare Industry: Healthcare organizations handle extremely sensitive data, including patient medical records. DDR can monitor access to these records, ensuring that only authorized individuals are accessing them. If an unauthorized access attempt is detected, DDR would alert the security team and block the attempt, safeguarding patient privacy.
- Financial Services: Financial institutions manage vast amounts of sensitive data, including account information and transaction history. DDR can detect patterns of fraudulent activity, such as repeated login attempts or large transfers to unfamiliar accounts. Once detected, DDR can halt these transactions and alert the security team.
- Manufacturing Industry: Manufacturers often rely on proprietary designs and processes, making them targets for industrial espionage. DDR can detect unauthorized access or copying of these valuable digital assets. It can then isolate the affected systems and neutralize the threat.
- Information Technology: In the IT sector, DDR can protect against threats like ransomware attacks. For example, if DDR detects a sudden increase in file encryption (a common sign of a ransomware attack), it can isolate the affected systems to prevent the spread of the attack and alert the security team.
In summary, DDR is a versatile and proactive security solution that can be used across a wide range of industries to protect valuable data. It's like having a digital security guard, constantly on duty to detect and respond to any potential threats.
DDR vs CSPM and DSPM
In the rapidly evolving world of data security, understanding the tools at your disposal is key to protecting your valuable information. Three of these tools - Data Detection and Response (DDR), Cloud Security Posture Management (CSPM), and Data Security Platform Management (DSPM) - each offer unique benefits. But what are the differences between them, and which one is right for your business?
Data Detection and Response (DDR)
Think of DDR as your digital security guard, constantly patrolling your data landscape. DDR uses advanced algorithms to continuously monitor your data, actively seeking out threats and taking swift action when something suspicious is detected. Whether it's an unauthorized access attempt or a sudden surge in data transfers, DDR is there to detect, investigate, and respond. DDR is an excellent choice if you're looking for comprehensive, around-the-clock protection for your data.
Cloud Security Posture Management (CSPM)
CSPM is like a building inspector for your cloud environments. It helps ensure that your cloud configurations are secure and comply with best practices and regulatory standards. If CSPM finds a misconfiguration that could potentially expose your data to threats, it flags it for your team to fix. If your business uses cloud services extensively, CSPM can be an essential tool to manage your cloud security.
Data Security Platform Management (DSPM)
DSPM is more like a comprehensive security control center. It integrates several security solutions, including DDR and CSPM, into a single platform. DSPM provides a unified view of your security landscape, making it easier to manage and coordinate your security efforts. If you're dealing with large volumes of data across multiple platforms and services, DSPM can help streamline your security management process.
While DDR, CSPM, and DSPM each offer unique advantages, they're not mutually exclusive. In fact, many businesses find that a combination of these tools provides the most effective protection. At Sotero, we can help you assess your data security needs and choose the right combination of DDR, CSPM, and DSPM to protect your valuable digital assets. Contact us today to learn more.
Getting Started with DDR
Stepping into the world of Data Detection and Response (DDR) might seem daunting, but it's simpler than you think, especially with the right partner by your side. Here's how you can get started with DDR:
- Assess Your Needs: Every business is unique, and so are its data security needs. Start by evaluating what kind of data you handle and what potential threats you might face. Are you storing sensitive customer information? Do you handle proprietary business secrets? The answers to these questions will help guide your DDR strategy.
- Understand DDR: DDR is a powerful tool, but to make the most of it, you need to understand what it does. Take some time to learn about its capabilities - how it detects, investigates, and responds to threats. Remember, DDR is like a 24/7 digital security guard for your data.
- Choose the Right Partner: Implementing DDR isn't something you have to do alone. By choosing the right data security partner, you can leverage their expertise to ensure your DDR strategy is tailored to your specific needs. Look for a partner that can offer ongoing support and has a strong track record in data security.
- Implement DDR: With a clear understanding of your needs and the right partner at your side, you're ready to implement DDR. Your partner will guide you through the process, ensuring that DDR is integrated seamlessly into your existing systems.
- Monitor and Adjust: Once DDR is in place, it's important to continuously monitor its performance and adjust your strategy as needed. Your data security needs will evolve over time, and your DDR strategy should evolve with them.
At Sotero, we're committed to making data security as simple and effective as possible. Our team of experts is ready to guide you through every step of the DDR journey, providing personalized advice and support to ensure your data is protected.
Ready to connect?
Ready to get started with DDR? Contact us today, and let's take the first step toward securing your digital future together.
Strategy Session
This is your chance to discover how Sotero can help your organization with its data security needs.
We typically cover the following together:
- Review your data security challenges
- Explore potential use cases
- Learn about Sotero
- Discuss next steps
