The Data-Centric Approach
Data Discovery & Classification
Patented In-Use Encryption
Real-Time, Behavior-Based Threat Detection
The "Ransomware Solution" you're considering doesn't secure data!
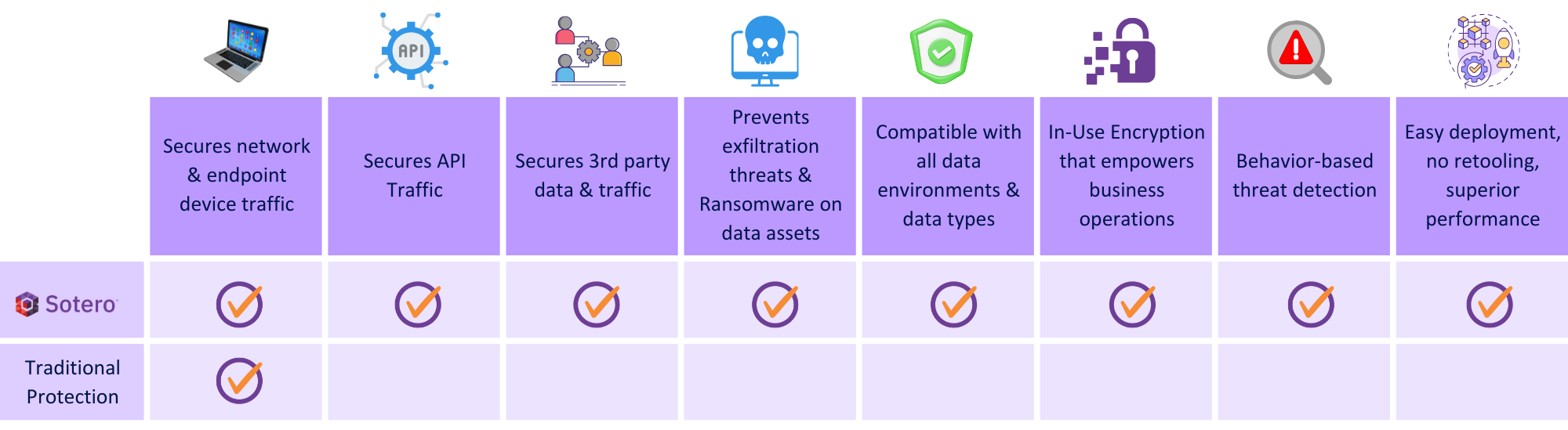
Disrupting The Cyber Threat Landscape Like None Other
Detects and stops attacks in minutes.
Granularly identifies any impacted assets for a rapid & total recovery.
Stolen data is unusable to attackers due to our patented in-use encryption.
Seamless integration across various cloud services & internal data stores for all data types.
Easy to use encryption & key management without latency
Simple deployment, scalable & agentless.
Maintains data compliance with regulatory, legal & governance mandates.
Securing your organization from ransomware is crucial, but with every security vendor promising "Ransomware Protection," it’s a daunting task to understand what each solution is capable of. Traditional endpoint and network security products are not sufficient to prevent the modern ransomware attack.
The key lies in securing all your sensitive data directly wherever it resides. By utilizing Sotero’s patented in-use encryption alongside our real-time behavior-based anomaly detection, Sotero detects, stops, and notifies about existing and zero-day threats that have bypassed perimeter defenses. Furthermore, as a fail-safe any data exfiltrated by attackers will be rendered useless and cannot be exploited because it remains encrypted.


